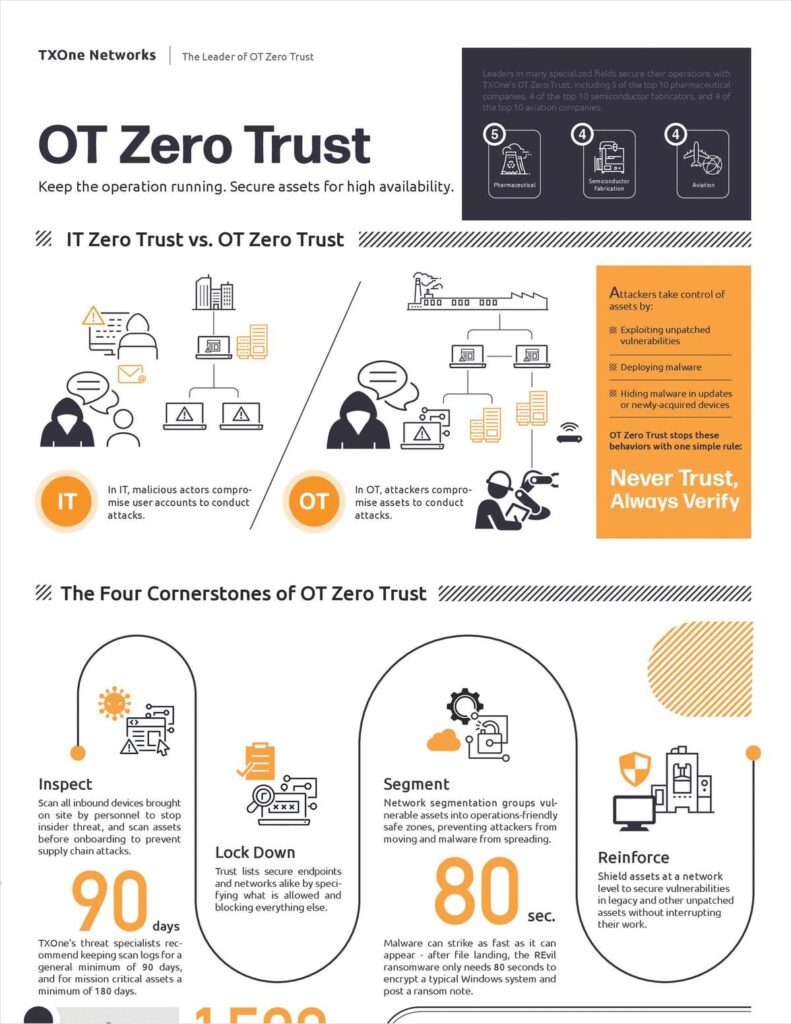
The philosophy of OT zero trust was developed as an answer to the problems traditional cyber defenses create in OT environments. IT cybersecurity uses a priority system called “CIA” - confidentiality first, integrity second, and availability third. OT network security, on the other hand, is based on asset activity so that productivity can always be the highest priority.
This requires a different model, “AIC” - availability is #1, integrity is #2, and confidentiality is #3. The OT Zero Trust approach prepares cyber defenses to never make assumptions about credibility and to continually evaluate trust on the network.
![]()